With the increased threat of cyberattacks, government agencies rely heavily on private contractors to have robust cybersecurity protections that will safeguard vital governmental data and information. When government contractors and grant recipients fail to meet required security obligations, they may face liability under the False Claims Act (FCA).
Whistleblowers play a critical role in uncovering the fraud that occurs when companies doing business with the government fail to meet required cybersecurity standards. As a reward for their efforts, whistleblowers are entitled to 15-30% of the money the government recovers in a successful FCA case.
A technology company agreed to pay $14.8 million to resolve FCA allegations that it misrepresented the development status and functionality of software it provided to the Government.
Following a number of high-profile cybersecurity incidents, the federal government is taking steps to improve the nation’s cybersecurity infrastructure. It has made cybersecurity an enforcement priority and is devoting additional resources to enforcement, upgrades, and strengthening technology standards. (See DOJ Highlights Importance of Whistleblowers and False Claims Act to Deter Cyber Fraud.)
Why is Cybersecurity a Priority?
Cybersecurity is the art of protecting networks, devices, and data from unauthorized access or criminal use. Cybersecurity is also the practice of ensuring confidentiality, integrity, and availability of information. Targets of cyber-attacks may include companies that:
-
- provide financial services
- host web and electronic mail services
- process security clearances
- use healthcare data or electronic medical records
- offer cloud-based services
- develop communications, satellite, and weapons systems
Without proper electronic system security measures in place, companies doing work with government agencies may jeopardize economic and national security interests.
What is Cybersecurity Fraud?
Cybersecurity fraud occurs when a company deceptively fails to meet cybersecurity requirements in its dealings with the government.
An electronic health records software company agreed to pay $57.25 million to resolve FCA allegations that it violated certification requirements and provided kickbacks to users to induce them to use and recommend the company’s EHR software.
Common cybersecurity failures targeted for FCA enforcement include:
-
- Knowing provision of deficient cybersecurity products or services. Entities that contract with the government must satisfy contractual requirements for the products and services they provide. Falsifying records to indicate compliance with contractual requirements, misrepresenting prices or discounts, concealing vulnerabilities, or failing to provide sufficient quality assurance may all give rise to FCA violations.
- Knowing failures to comply with cybersecurity standards. When government agencies acquire cyber products and services, they often require contractors and grantees to meet specific contract terms, which are often based on uniform contracting language or agency-specific requirements. For example, cybersecurity standards may require contractors to take measures to protect government data, to restrict non-U.S. citizen employees from accessing systems, or to avoid using components from certain foreign countries. The knowing failure to meet these cybersecurity standards deprives the government of what it bargained for.
- Knowing misrepresentation of security controls and practices. In seeking or performing under a government contract, companies often make representations to the government about their products, services, and cybersecurity practices. These representations may be about a system security plan detailing the security controls it has in place, the company’s practices for monitoring its systems for breaches, or password and access requirements. Misreporting implementation of or compliance with these practices may cause the government to choose a contractor that should not have received the contract in the first place. Or it could cause the government to structure a contract differently than it otherwise would have. Knowing misrepresentations of this kind also deprive the government of what it paid for and violate the FCA.
- Knowing failure to monitor and report suspected breaches. Government contracts for cyber products, as well as for other goods and services, often require the timely reporting of cyber incidents that could threaten the security of agency information and systems. Prompt reporting by contractors often is crucial for agencies to respond to a breach, remediate the vulnerability, and limit the resulting harm. Failure to comply with reporting requirements is another way a company may run afoul of the FCA.
Who Can Blow the Whistle on Cybersecurity Fraud?
The FCA is a powerful tool to make companies accountable when they allow or fail to address cybersecurity flaws in their products, systems, and management of government information. Such flaws can threaten software and systems purchased and used by government agencies.
IT company insiders and security experts often have critical information about cybersecurity flaws that are not evident to the government. Additionally, program managers, system designers and developers, software engineers, contracting officers, chief information officers, and security officers may all be in a position to identify and report fraudulent conduct – and be rewarded for their efforts through the FCA.
A company providing security surveillance software agreed to pay $8.6 million to resolve FCA allegations that it concealed vulnerabilities in its product and failed to report the security flaws to the government. The flaws would permit unauthorized access to the system, with the potential for hackers to control or manipulate security cameras and the recorded footage.
Cybersecurity and the Department of Defense
The Department of Defense, General Services Administration, and NASA amended the Federal Acquisition Regulation (FAR) to add a new subpart and contract clause on safeguarding information systems containing federal contract information. As a baseline, federal contractors and subcontractors are required to comply with basic cybersecurity controls established in the National Institute of Standards and Technology (NIST) Special Publication 800-171. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems. If a contracting entity fails to comply with NIST standards, it could face FCA liability.
A telecom software company agreed to pay $11.4 million to resolve FCA allegations that it used employees without security clearances to perform contract work for the Defense Information Systems Agency (DISA).
Federal contractors and subcontractors comprise the Defense Industrial Base (DIB) Sector, a worldwide industrial complex providing products and services that are essential to mobilize, deploy, and sustain military operations and weapons systems. The DIB consists of more than 100,000 companies and their subcontractors who perform under contract with the Department of Defense (DOD) and government-owned/government-operated facilities. The DIB develops and maintains sensitive technology and intellectual property vital to protecting and defending national security. As a consequence, malicious cyber actors regularly target the DIB and look for ways to access company networks and obtain valuable information that may compromise national security and warfighting capabilities.
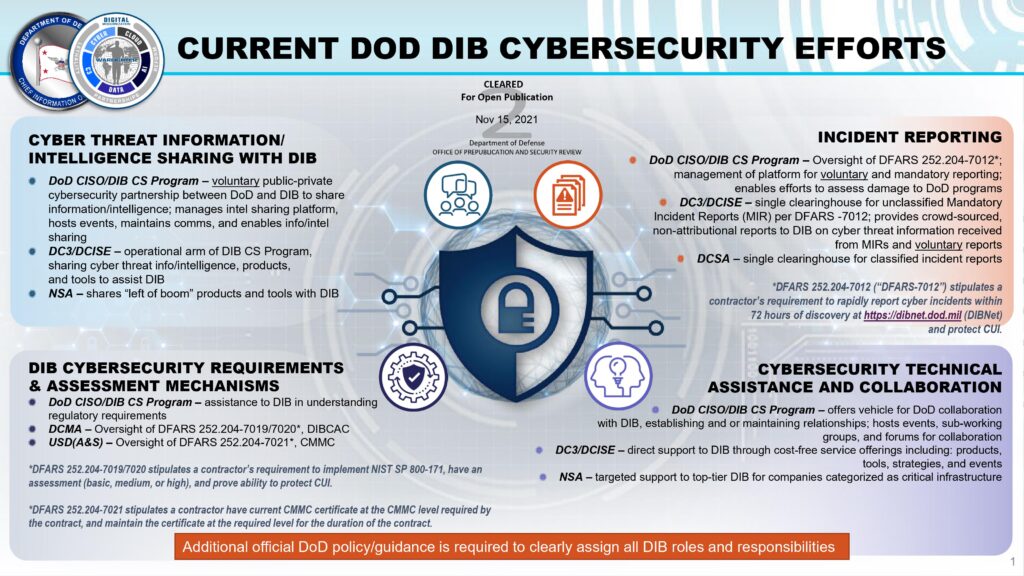
DIB and Cybersecurity Maturity Model Certification (CMMC)
The Cybersecurity Maturity Model Certification (CMMC) program enhances cyber protection standards for companies in the DIB. It is designed to protect sensitive information that is shared by the DOD with its contractors and subcontractors, including Controlled Unclassified Information (CUI) (information that is not classified but requires safeguarding or dissemination controls) and Federal Contract Information (FCI) (information, not intended for public release, provided by or generated by the government under a contract to develop or deliver a product or service for the government).
The protection of CUI and FCI held in nonfederal systems and organizations is of paramount importance to federal agencies and can directly impact the ability of the federal government to successfully conduct its essential functions. The CMMC program incorporates a set of cybersecurity requirements into acquisition contracts and provides the DOD with increased assurance that contractors and subcontractors are meeting these requirements. Under the CMMC, DIB contractors will be required to:
-
- Implement certain cybersecurity standards;
- Perform self-assessments; and/or
- Obtain third-party certification requirements are being met
These conditions will need to be satisfied for a DOD contract to be awarded. Though not yet fully incorporated into DOD contracts, this will be an area ripe for FCA fraud if companies fail to adhere to the new requirements – and whistleblowers will be essential to uncover and report a DIB contractors’ misconduct. For example, a company may submit its self-assessment affirmations knowing that those affirmations are false or incorrect, and only an insider, consultant, or competitor may know this fact. If you are aware of a company failing to meet cybersecurity requirements, contact a cybersecurity False Claims Act attorney.
Contact Halunen Law Cybersecurity Fraud Attorneys
If you know about a cybersecurity fraud scheme or any other form of fraud against the government, the whistleblower attorneys at Halunen Law stand ready to support you as you consider whether and how to report the misconduct. We have recovered billions of dollars working with whistleblowers who had the courage to do the right thing and millions of dollars in compensation for individuals who experienced retaliation.


